Technology
There may be stalking software on your Android phone – here’s how to remove it

Consumer-grade spy apps that secretly and always monitor your private messages, photos, phone calls and site in real time are a growing problem for Android users.
This guide will show you how to discover and remove popular monitoring apps from your Android phone, including TheTruthSpy, KidsGuard, and other apps.
READ OUR EXCLUSIVE STUDY
Consumer spy apps are sometimes sold under the guise of kid or family monitoring software, but are referred to as “stalkerware” and “spouseware” due to their ability to track and monitor partners or spouses without their consent. These spy apps are downloaded from outside the Google Play app store, installed on the phone without the person’s consent, and infrequently disappear from the house screen to avoid detection.
Stalkerware apps use built-in Android features which are typically utilized by firms to remotely manage worker work phones or use Android’s availability mode to spy on someone’s device.
You may notice that your phone is acting unusually, running hotter or slower than usual, or using loads of network data, even if you’re not actively using it.
Checking if your Android device has been tampered with can be done quickly and simply.
Before you begin
It’s vital to have a security plan and reliable support in the event you need it. Remember that removing spyware from your phone will likely alert the one that placed it, which could create a dangerous situation. The Coalition Against Stalkerware offers advice and guidance for victims and survivors of stalkerware.
Please note that this guide only helps you discover and remove spyware applications, and doesn’t remove data that has already been collected and uploaded to servers. Additionally, some versions of Android may have barely different menu options. As at all times with any advice, you follow these steps at your own risk.
Check your Google Play Protect settings
Make sure Google Play Protect, a security feature on Android phones, is turned on. Image credits: TechCrunch
Google Play Protect is among the finest anti-malicious app protections on Android, checking apps downloaded from the Google app store and third-party sources for signs of probably malicious activity. These protections stop working if you turn off Play Protect. It’s vital to turn on Play Protect to be certain that it’s working and scanning for malicious apps.
You can check whether Play Protect is enabled within the Play Store app settings. You may also scan for malicious applications in the event you have not already scanned.
Verify that Accessibility Services has not been affected
Stalkerware uses deep device access to access data and has been known to abuse Android Accessibility Mode, which by design requires more extensive access to the operating system and data for screen readers and other accessibility features to function.
Android users who don’t use apps or accessibility features mustn’t see any apps of their Android settings.
If you do not recognize the downloaded service in your accessibility options, you possibly can disable it in your settings and delete the app. Some stalkerware apps disguise themselves as normal-looking apps and are sometimes called “Accessibility”, “Device Status”, “System Service” or other innocuous-sounding names.
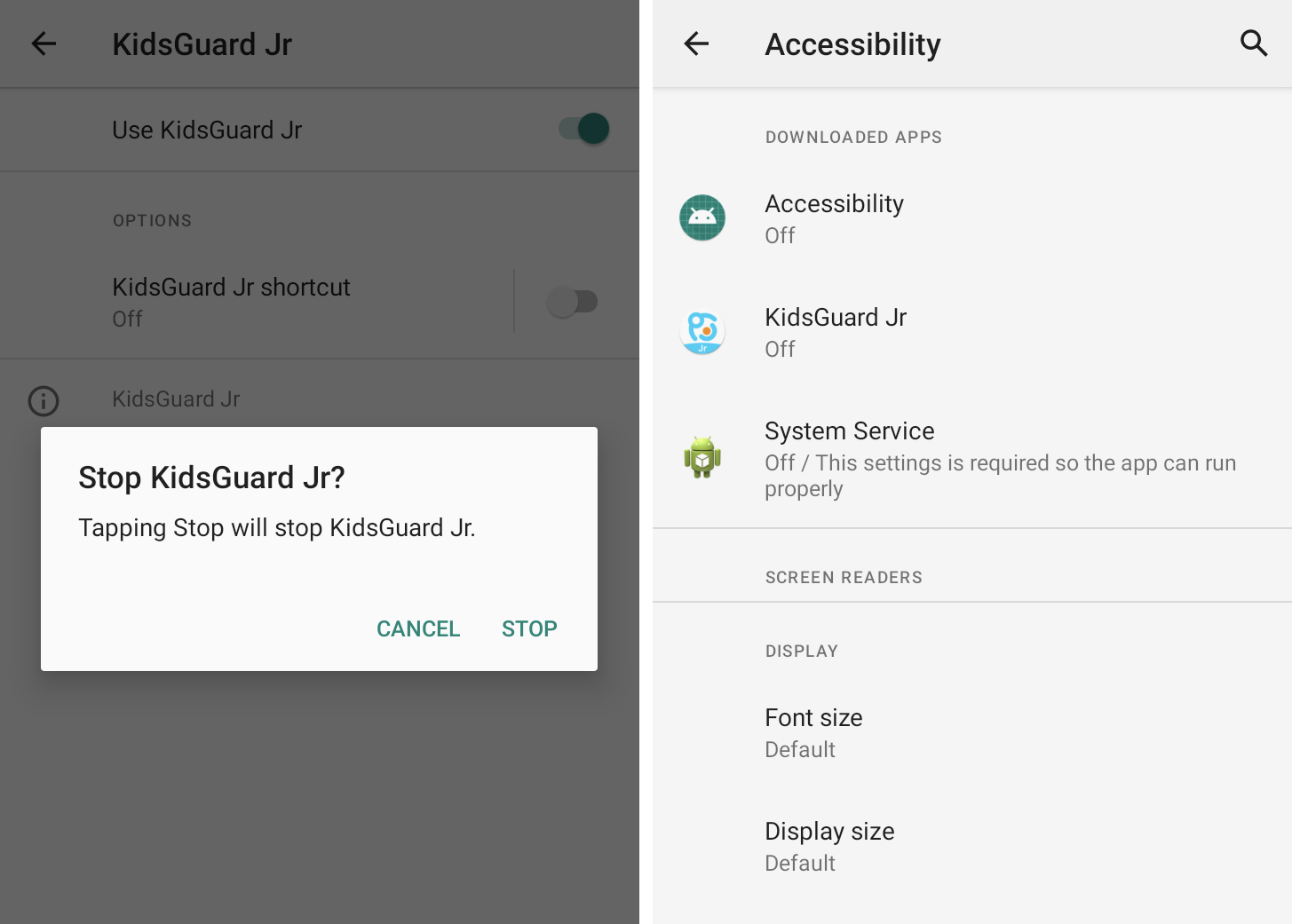
Android spyware often abuses built-in accessibility features. Image credits: TechCrunch
Check your access to notifications
Like accessibility features, Android also allows third-party apps to access and skim incoming notifications, corresponding to allowing smart speakers to read alerts aloud or display in-automotive notifications on the dashboard. Granting notification access to the Stalkerware app allows you to always monitor your notifications, including messages and other alerts.
You can check which apps have access to your notifications by checking your Android notification access settings under Special app access. You may recognize a few of these apps, corresponding to Android Auto. You can turn off notification access for any app you do not recognize.
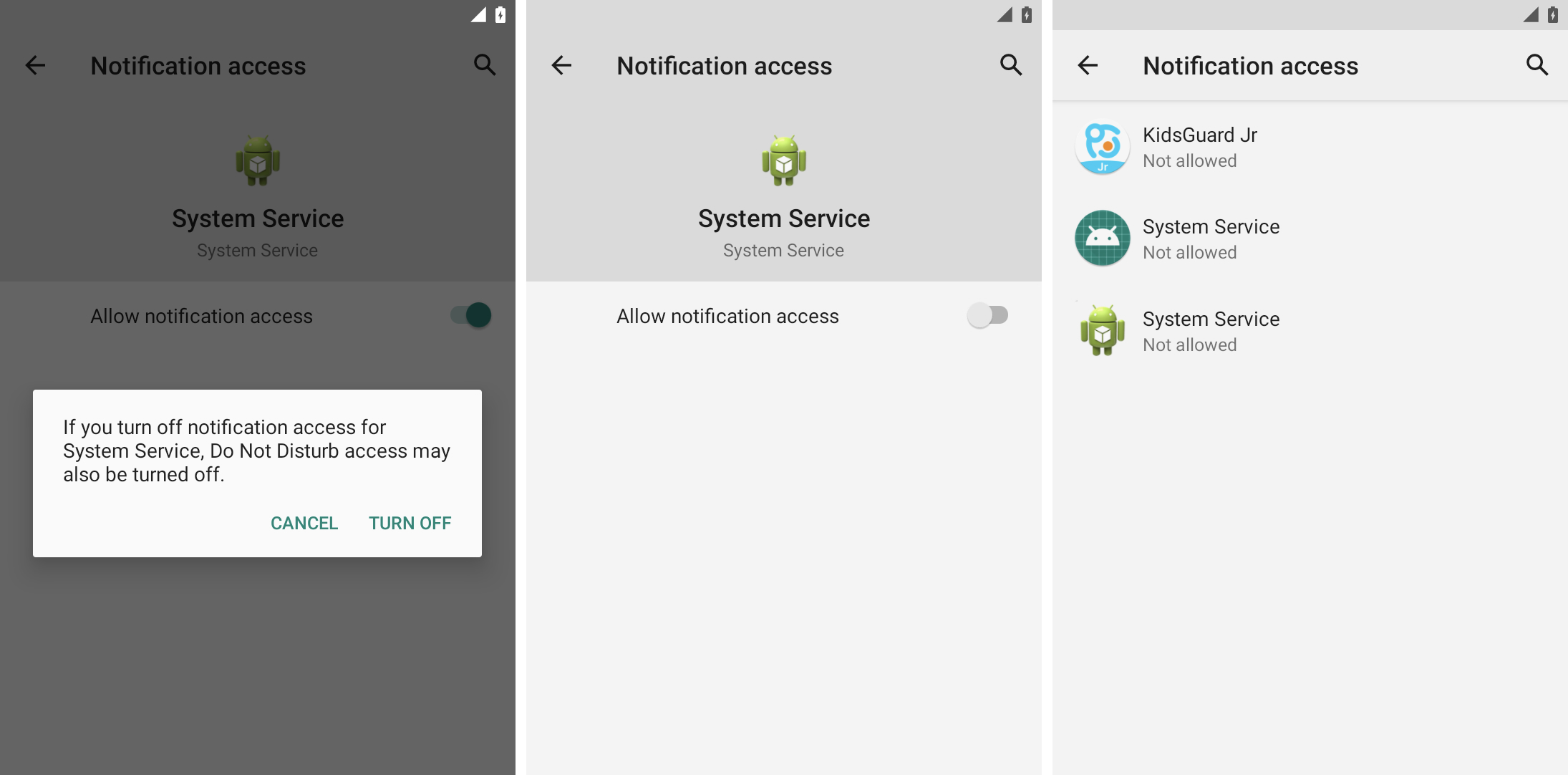
Spyware uses access to notifications to read user messages and other alerts. Image credits: TechCrunch
Check if the device administration application is installed
Other features often abused by stalkerware include Android Device Administrator options, which give similar but even broader access to Android devices and user data.
Device administrator options are typically utilized by firms to remotely manage their employees’ phones, for instance to wipe the phone if the device is stolen to prevent data loss. But these features also allow stalkerware apps to spy on your Android display and device data.
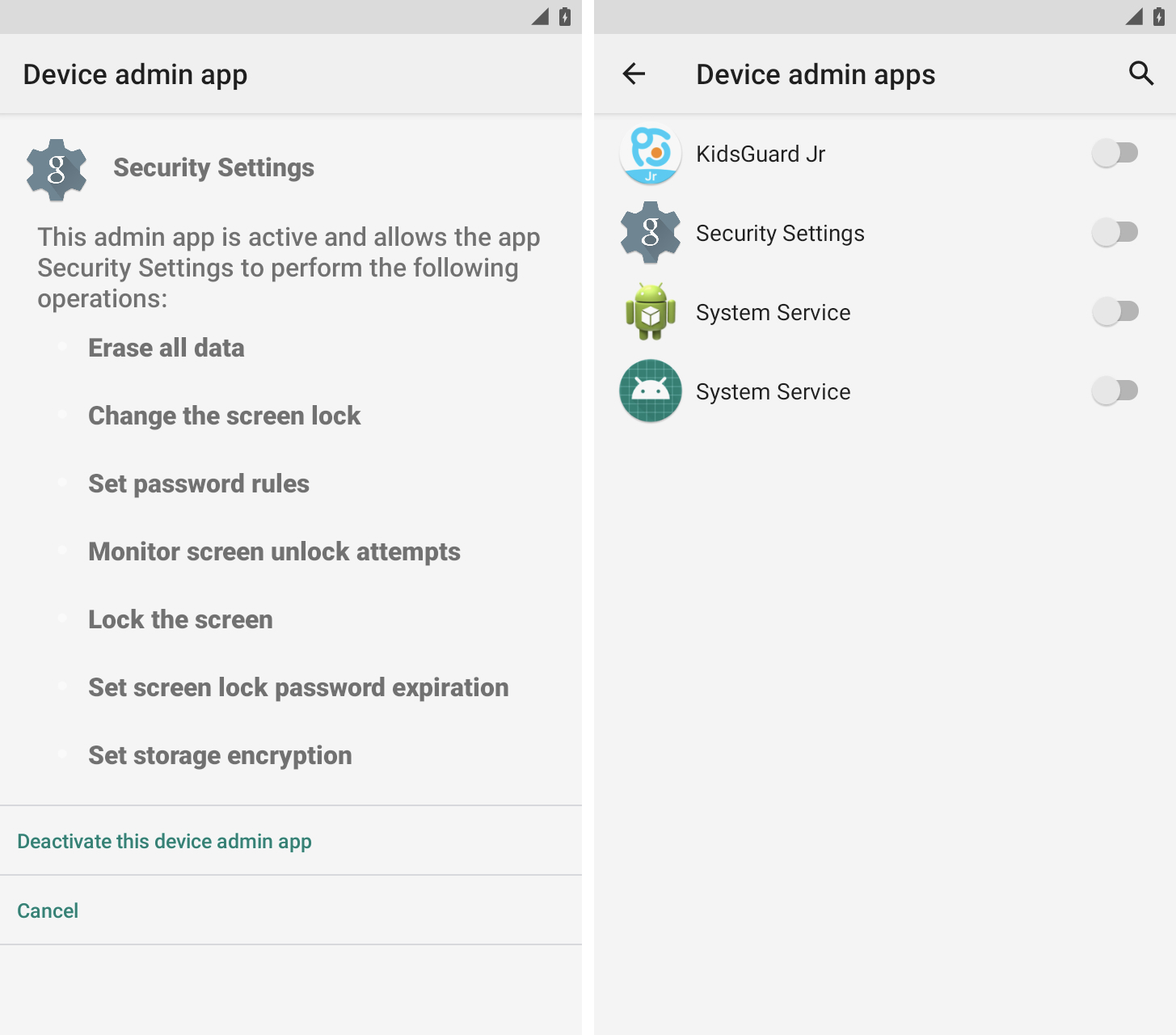
An unrecognized item in your device’s admin app settings is a standard indicator that your phone has been compromised. Image credits: TechCrunch
You can find the device administrator app settings in Settings within the Security section.
Most people do not have a tool administration app on their personal phone, so be wary in the event you see an app you do not recognize with a similarly vague and confusing name, corresponding to “System Service,” “Device Health,” or “Device Administrator.”
Check for apps to uninstall
The icon for any of those stalkerware apps may not be visible on your home screen, but they are going to still appear within the app list on your Android device.
You can see all installed apps in Android settings. Look for apps and icons you do not recognize. These apps may also appear as having broad access to your calendar, call logs, camera, contacts, and site data.
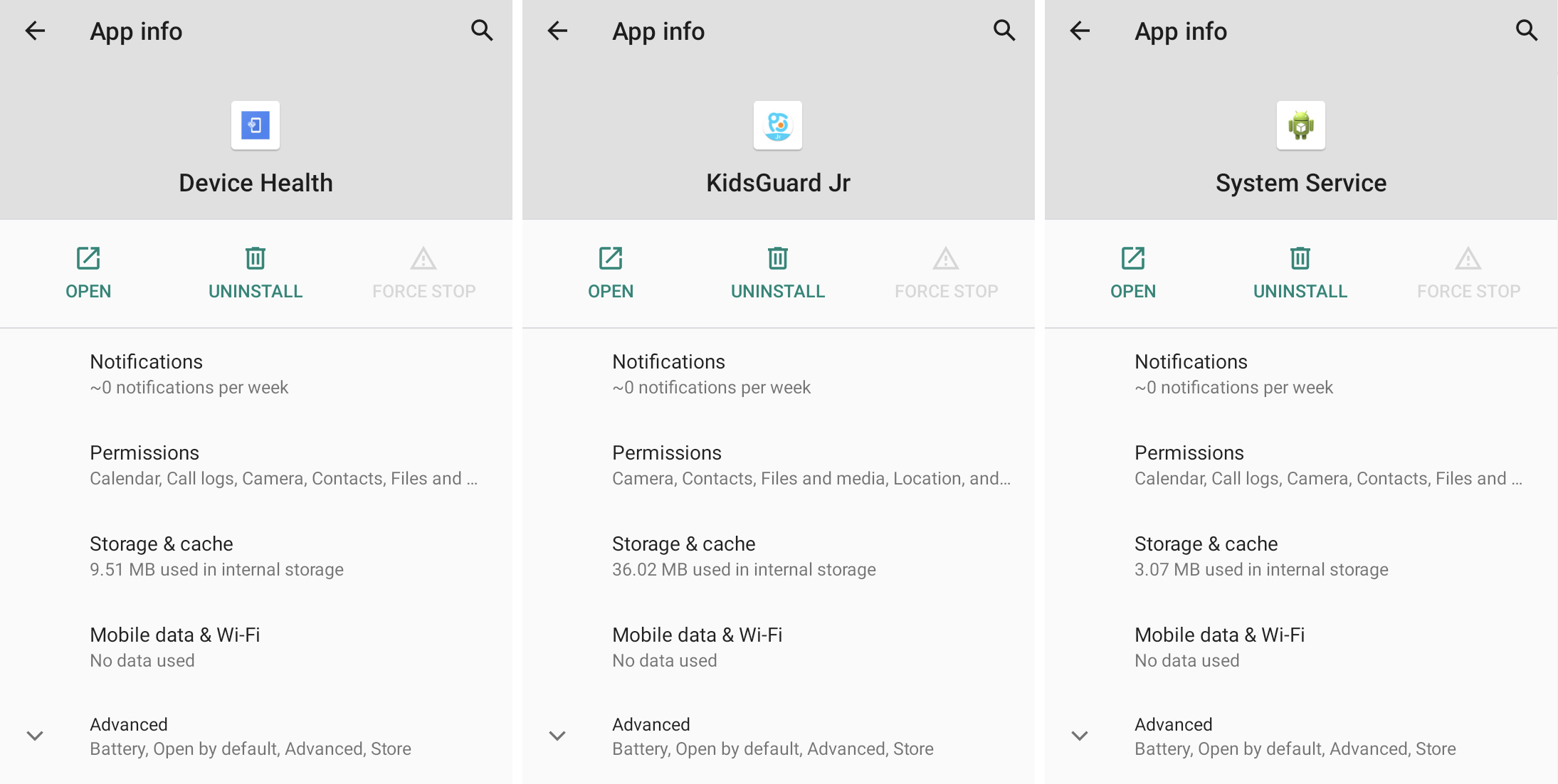
Spyware applications are designed to mix in with generic-looking names and icons. Image credits: TechCrunch
Forcefully stopping and uninstalling a stalkerware application will likely notify the one that installed the stalkerware that the applying isn’t any longer working.
Secure your device
If you have got stalkerware installed on your phone, there may be a high likelihood that your phone has been unlocked, unprotected, or that the screen lock has been guessed or known. A stronger lock screen password can assist protect your phone from intruders. You also needs to protect your email and other online accounts by utilizing two-factor authentication when possible.
Read more on TechCrunch:
Technology
The latest model AI Google Gemma can work on phones

It grows “open” AI Google, Gemma, grows.
While Google I/O 2025 On Tuesday, Google removed Gemma 3N compresses, a model designed for “liquid” on phones, laptops and tablets. According to Google, available in a preview starting on Tuesday, Gemma 3N can support sound, text, paintings and flicks.
Models efficient enough to operate in offline mode and without the necessity to calculate within the cloud have gained popularity within the AI community lately. They will not be only cheaper to make use of than large models, but they keep privacy, eliminating the necessity to send data to a distant data center.
During the speech to I/O product manager, Gemma Gus Martins said that GEMMA 3N can work on devices with lower than 2 GB of RAM. “Gemma 3N shares the same architecture as Gemini Nano, and is also designed for incredible performance,” he added.
In addition to Gemma 3N, Google releases Medgemma through the AI developer foundation program. According to Medgemma, it’s essentially the most talented model to research text and health -related images.
“Medgemma (IS) OUR (…) A collection of open models to understand the text and multimodal image (health),” said Martins. “Medgemma works great in various imaging and text applications, thanks to which developers (…) could adapt the models to their own health applications.”
Also on the horizon there may be SignGEMMA, an open model for signaling sign language right into a spoken language. Google claims that Signgemma will allow programmers to create recent applications and integration for users of deaf and hard.
“SIGNGEMMA is a new family of models trained to translate sign language into a spoken text, but preferably in the American sign and English,” said Martins. “This is the most talented model of understanding sign language in history and we are looking forward to you-programmers, deaf and hard communities-to take this base and build with it.”
It is value noting that Gemma has been criticized for non -standard, non -standard license conditions, which in accordance with some developers adopted models with a dangerous proposal. However, this didn’t discourage programmers from downloading Gemma models tens of tens of millions of times.
.
(Tagstransate) gemma
Technology
Trump to sign a criminalizing account of porn revenge and clear deep cabinets

President Donald Trump is predicted to sign the act on Take It Down, a bilateral law that introduces more severe punishments for distributing clear images, including deep wardrobes and pornography of revenge.
The Act criminalizes the publication of such photos, regardless of whether or not they are authentic or generated AI. Whoever publishes photos or videos can face penalty, including a advantageous, deprivation of liberty and restitution.
According to the brand new law, media firms and web platforms must remove such materials inside 48 hours of termination of the victim. Platforms must also take steps to remove the duplicate content.
Many states have already banned clear sexual desems and pornography of revenge, but for the primary time federal regulatory authorities will enter to impose restrictions on web firms.
The first lady Melania Trump lobbyed for the law, which was sponsored by the senators Ted Cruz (R-TEXAS) and Amy Klobuchar (d-minn.). Cruz said he inspired him to act after hearing that Snapchat for nearly a 12 months refused to remove a deep displacement of a 14-year-old girl.
Proponents of freedom of speech and a group of digital rights aroused concerns, saying that the law is Too wide And it will probably lead to censorship of legal photos, similar to legal pornography, in addition to government critics.
(Tagstransate) AI
Technology
Microsoft Nadella sata chooses chatbots on the podcasts

While the general director of Microsoft, Satya Nadella, says that he likes podcasts, perhaps he didn’t take heed to them anymore.
That the treat is approaching at the end longer profile Bloomberg NadellaFocusing on the strategy of artificial intelligence Microsoft and its complicated relations with Opeli. To illustrate how much she uses Copilot’s AI assistant in her day by day life, Nadella said that as a substitute of listening to podcasts, she now sends transcription to Copilot, after which talks to Copilot with the content when driving to the office.
In addition, Nadella – who jokingly described her work as a “E -Mail driver” – said that it consists of a minimum of 10 custom agents developed in Copilot Studio to sum up E -Mailes and news, preparing for meetings and performing other tasks in the office.
It seems that AI is already transforming Microsoft in a more significant way, and programmers supposedly the most difficult hit in the company’s last dismissals, shortly after Nadella stated that the 30% of the company’s code was written by AI.
(Tagstotransate) microsoft
-

 Press Release1 year ago
Press Release1 year agoU.S.-Africa Chamber of Commerce Appoints Robert Alexander of 360WiseMedia as Board Director
-

 Press Release1 year ago
Press Release1 year agoCEO of 360WiSE Launches Mentorship Program in Overtown Miami FL
-

 Business and Finance12 months ago
Business and Finance12 months agoThe Importance of Owning Your Distribution Media Platform
-

 Business and Finance1 year ago
Business and Finance1 year ago360Wise Media and McDonald’s NY Tri-State Owner Operators Celebrate Success of “Faces of Black History” Campaign with Over 2 Million Event Visits
-

 Ben Crump1 year ago
Ben Crump1 year agoAnother lawsuit accuses Google of bias against Black minority employees
-

 Theater1 year ago
Theater1 year agoTelling the story of the Apollo Theater
-

 Ben Crump1 year ago
Ben Crump1 year agoHenrietta Lacks’ family members reach an agreement after her cells undergo advanced medical tests
-

 Ben Crump1 year ago
Ben Crump1 year agoThe families of George Floyd and Daunte Wright hold an emotional press conference in Minneapolis
-

 Theater1 year ago
Theater1 year agoApplications open for the 2020-2021 Soul Producing National Black Theater residency – Black Theater Matters
-

 Theater12 months ago
Theater12 months agoCultural icon Apollo Theater sets new goals on the occasion of its 85th anniversary



















